
A intelligent, new phishing approach makes use of Microsoft Edge WebView2 functions to steal sufferer’s authentication cookies, permitting menace actors to bypass multi-factor authentication when logging into stolen accounts.
With the massive variety of information breaches, distant entry trojan assaults, and phishing campaigns, stolen login credentials have change into plentiful.
Nonetheless, the rising adoption of multi-factor authentication (MFA) has made it troublesome to make use of these stolen credentials until the menace actor additionally has entry to the goal’s one-time MFA passcodes or safety keys.
This has led to menace actors and researchers developing with new methods of bypassing MFA, together with zero-day web site vulnerabilities, reverse proxies, and intelligent strategies, such because the Browser within the Browser assault and using VNC to show distant browsers regionally.
This week, cybersecurity researcher mr.d0x has created a brand new phishing technique that makes use of Microsoft Edge WebView2 functions to simply steal a person’s authentication cookies and log into stolen accounts, even when they’re secured with MFA.
Microsoft Edge WebView2 to the rescue
This new social engineering assault is known as WebView2-Cookie-Stealer and consists of a WebView2 executable that, when launched, opens up a reliable web site’s login kind inside the appliance.
Microsoft Edge WebView2 means that you can embed an online browser, with full assist for HTML, CSS, and JavaScript, instantly in your native apps utilizing Microsoft Edge (Chromium) because the rendering engine.
Utilizing this know-how, apps can load any web site right into a native software and have it seem as it might in case you opened it in Microsoft Edge.
Nonetheless, WebView2 additionally permits a developer to instantly entry cookies and inject JavaScript into the webpage that’s loaded by an software, making it a superb device to log keystrokes and steal authentication cookies after which ship them to a distant server.
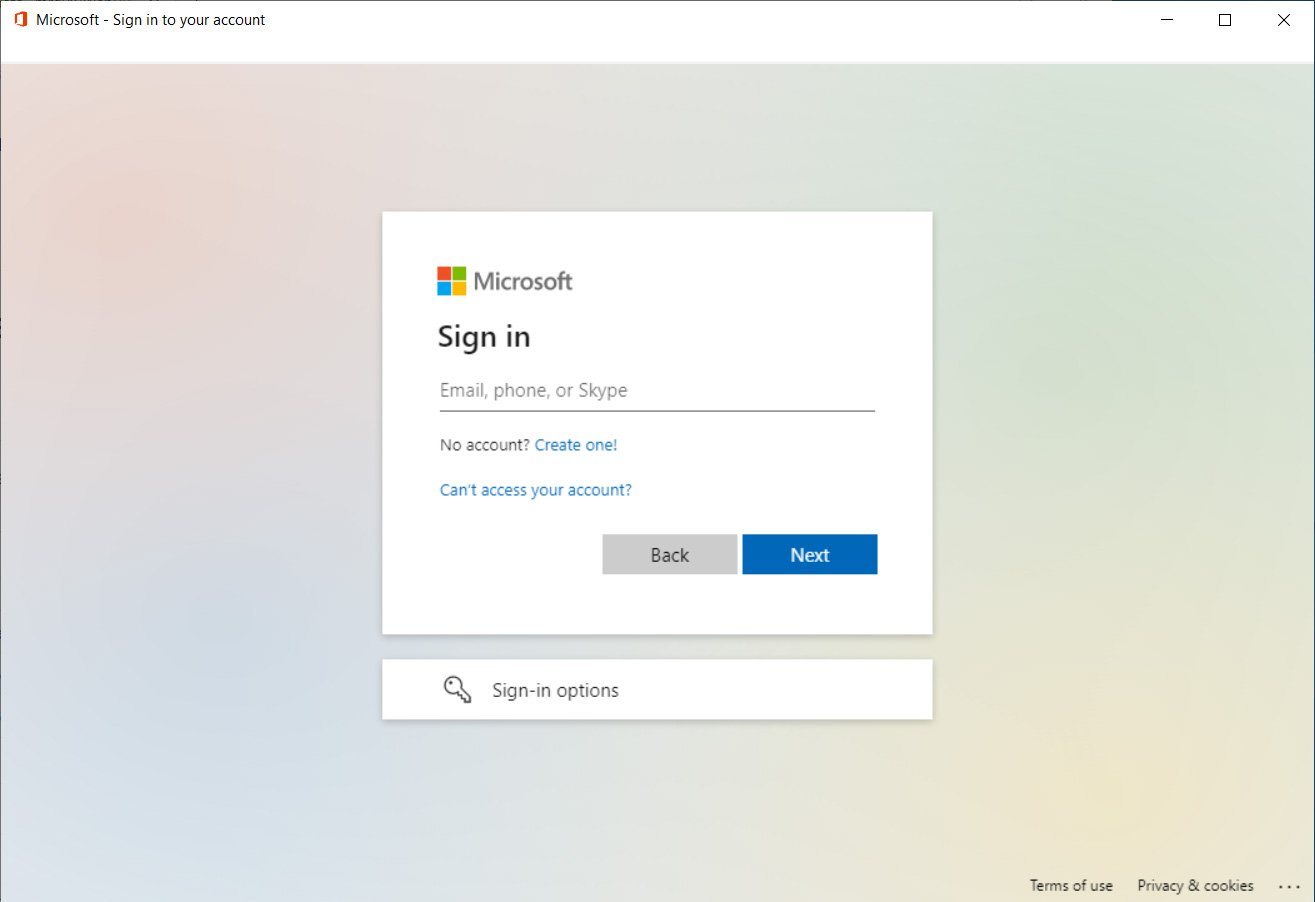
Within the new assault by mr.d0x, the proof-of-concept executable will open the reliable Microsoft login kind utilizing the embedded WebView2 management.
As you possibly can see under, the login kind renders precisely as it might when utilizing a daily browser and doesn’t include any suspicious components like typos, unusual domains, and many others.
Supply: BleepingComputer
As a WebView2 software can inject JavaScript into the web page, something the person sorts is routinely despatched again to the attacker’s internet server.
Nonetheless, the true energy of the sort of software is the flexibility to steal any cookies despatched by the distant server after a person logs in, together with authentication cookies.
To do that, mr.d0x instructed BleepingComputer that the appliance creates a Chromium Consumer Information folder the primary time it runs after which makes use of that folder for every subsequent set up.
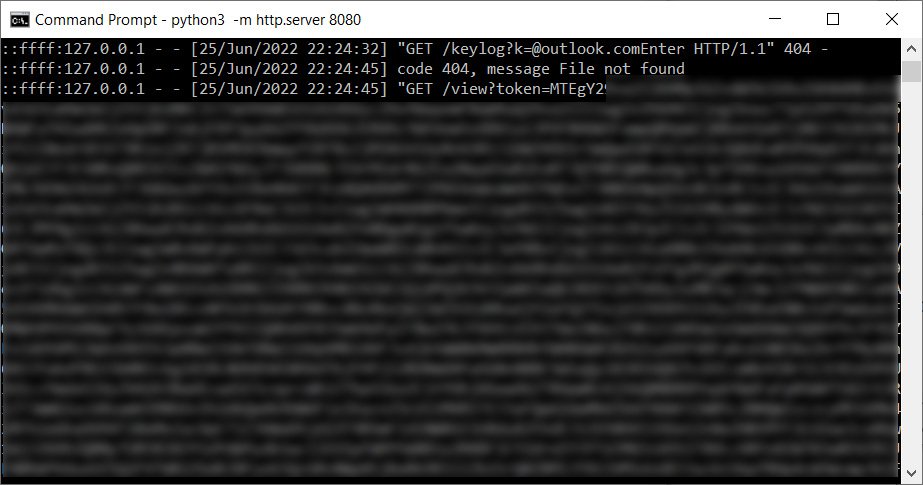
The malicious software then makes use of the built-in WebView2 ‘ICoreWebView2CookieManager’ interface to export the positioning’s cookies on profitable authentication and sends them again to the attacker-controlled server, as proven under.
Supply: BleepingComputer
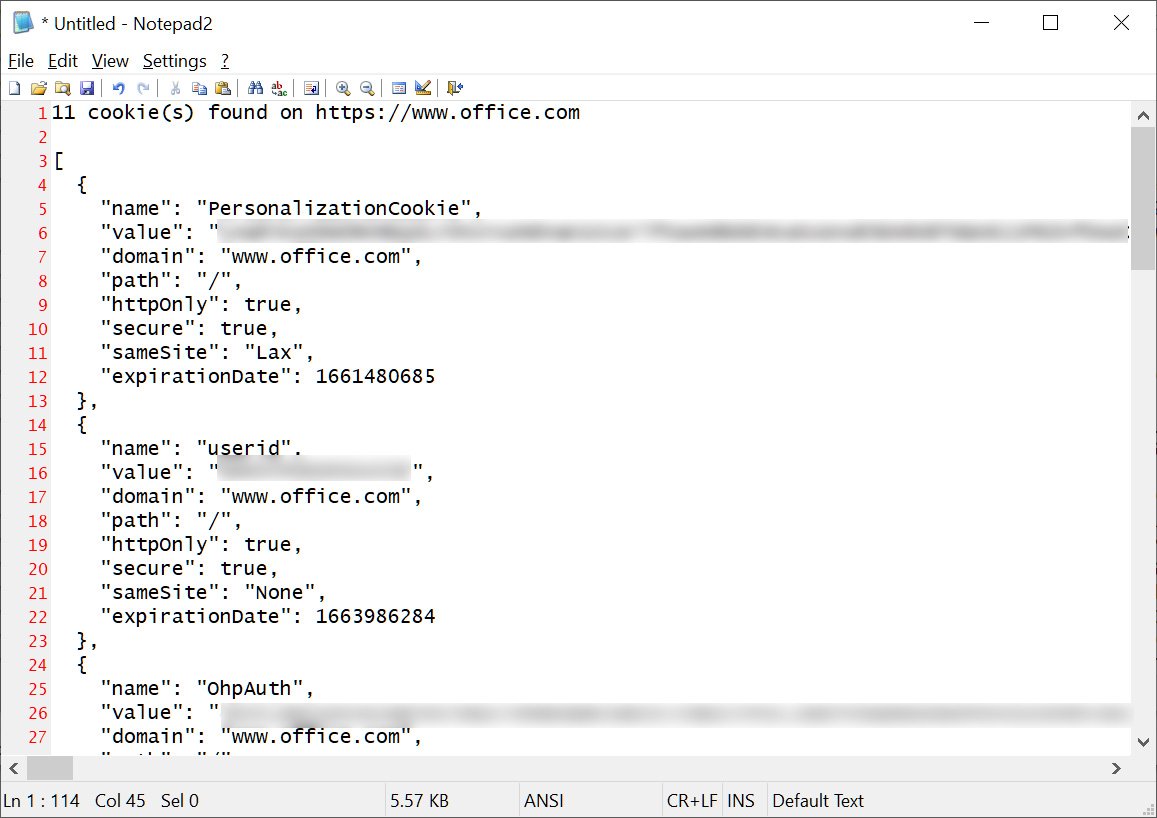
As soon as the attacker decodes the base64-encoded cookies, they are going to have full entry to the authentication cookies for the positioning and may use them to log in to a person’s account.
Supply: BleepingComputer
The researcher additionally discovered that it was attainable to make use of the WebView2 app to steal cookies for an current Chrome person profile by copying their current Chromium profile.
“WebView2 can be utilized to steal all out there cookies for the present person. This was efficiently examined on Chrome,” explains a report on this method by mr.d0x.
“WebView2 means that you can launch with an current Consumer Information Folder (UDF) reasonably than creating a brand new one. The UDF accommodates all passwords, classes, bookmarks and many others. Chrome’s UDF is positioned at C:CustomersAppDataLocalGoogleChromeUser Information.”
“We are able to merely inform WebView2 to start out the occasion utilizing this profile and upon launch extract all cookies and switch them to the attacker’s server.”
When requested how an attacker may use these cookies, mr.d0x instructed BleepingComputer that they might go to the login kind for an account they stole and import the cookies utilizing a Chrome extension like ‘EditThisCookie.’ As soon as the cookies are imported, they merely refresh the web page to routinely be authenticated on the positioning.
What’s extra regarding, although, is that this assault additionally bypasses MFA secured by OTPs or safety keys, because the cookies are stolen after the person logged in and efficiently solved their multi-factor authentication problem.
“So let’s imagine the attacker units up Github.com/login of their webview2 app, and the person logs in, then cookies could be extracted and exfil’d to the attacker’s server.”
“Yubikeys cannot prevent since you’re authenticating to the REAL web site not a phishing web site.”
mr.d0x
Moreover, these cookies will likely be legitimate till the session expires or there may be another post-authentication verify that detects uncommon conduct.
“So until they’ve some extra checks POST-AUTHENTICATION then that will not be detected, and naturally this isn’t really easy to implement,” mr.d0x instructed BleepingComputer.
Assault requires social engineering
Nonetheless, as mr.d0x admits and Microsoft identified of their response to our questions, this assault is a social engineering assault and requires a person to run a malicious executable.
“This social engineering approach requires an attacker to persuade a person to obtain and run a malicious software,” Microsoft instructed BleepingComputer in an announcement relating to this new approach.
“We advocate customers apply protected computing habits, keep away from working or putting in functions from unknown or untrusted sources, and hold Microsoft Defender (or different anti-malware software program) working and up-to-date.”
Due to this fact, getting somebody to run an software within the first place might take extra work.
With that stated, historical past has proven us that many individuals “simply run issues” with out fascinated by the ramifications, whether or not that be e mail attachments, random downloads off the Web, cracks and warez, and recreation cheats.
All of those strategies are confirmed to work with pretty little effort, resulting in the set up of ransomware, distant entry trojans, password stealing trojans, and extra.
Due to this fact, the researcher’s WebView2 assault is possible, particularly if created to appear to be a reliable software installer that requires you to log in first. For instance, a pretend Microsoft Workplace installer, recreation, or Zoom shopper.
Whereas this assault has not been seen utilized in real-world assaults, the researcher’s strategies have been rapidly utilized in assaults prior to now, so that is one thing that safety admins and professionals must control.
As for methods to shield your self from these assaults, all of the common cybersecurity recommendation stays the identical.
Don’t open unknown attachments, particularly if they’re executables, scan recordsdata you obtain from the Web and don’t enter your credentials into an software until you’re 100% certain this system is reliable.









